Usage and Permissions
In Serenity* Star, there are three main ways to control access and permissions for agents: API Keys, Users, and Groups. Below is a simple overview of how each works, how to configure them, and the main usage flows.
API Key Permissions
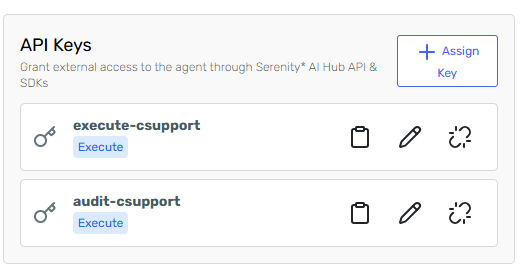
API Keys grant access to agents via the Serenity* Star API. Each key is assigned a specific permission for each agent, defining what actions are allowed. API Keys can be scoped to individual agents or, in some cases, have global access across all agents.
How to Add or Assign an API Key
-
Go to the agent's permissions section.
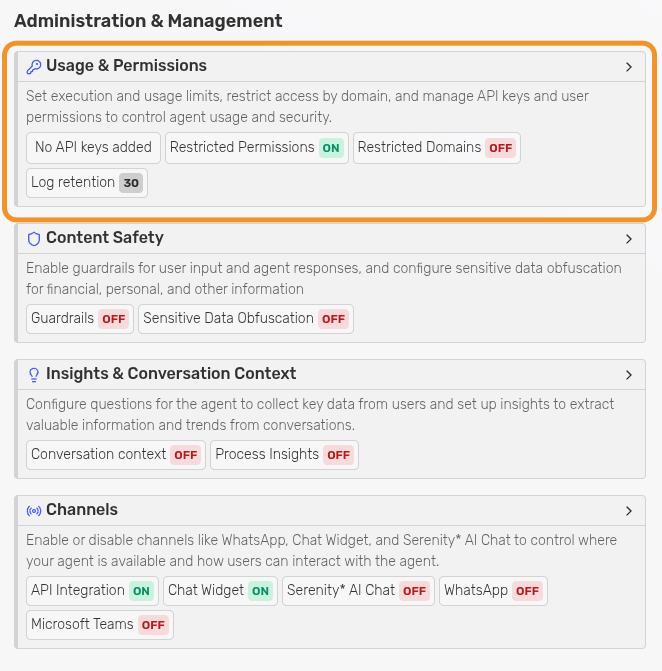
-
Click Assign Key.
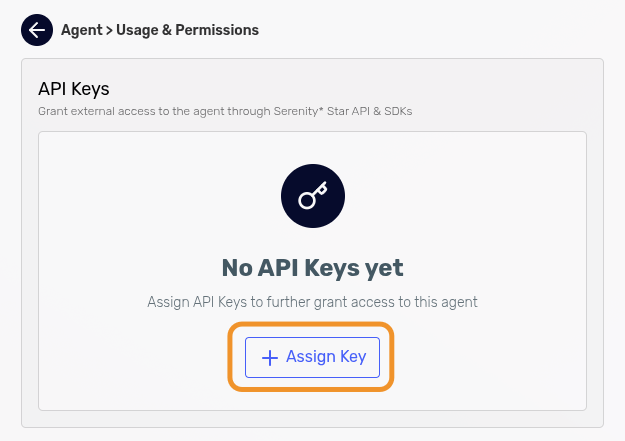
-
A side panel will open. You can select an existing key you own (only keys you created are shown), or create a new key directly from the side panel.
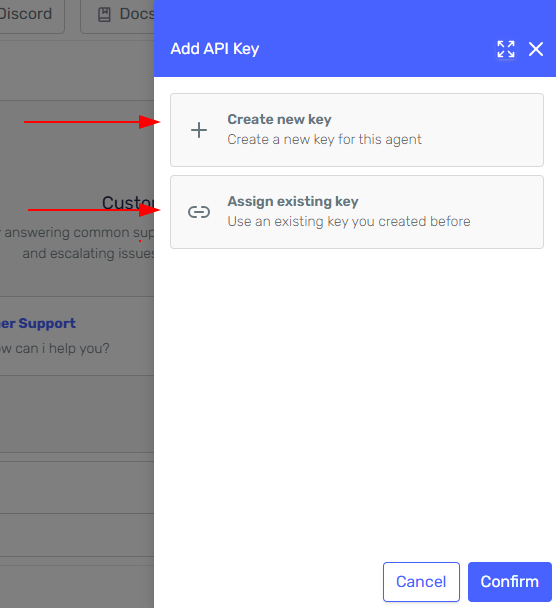
-
If creating a new key, enter a name and select the permission for this agent:
- Agent Administrator: Full access
- Agent Auditor: View logs/audit and execute the agent
- Agent Execution: Execute only
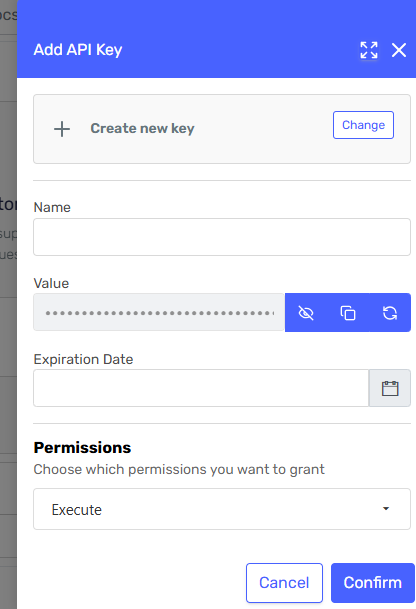
-
Click on "Confirm" to assign the new API key to the agent.
-
Once assigned, the key appears in the agent's key list.
- If you are the owner, you can edit its permission or unassign it.
- If you are not the owner, you can only unassign it from the agent.
Permission assignments only take effect when you Save the agent configuration.
API Key Scopes
API Keys in Serenity* Star have two possible scopes, which define their reach and how they are managed:
Agent Scope:
- Created directly from an agent's permissions section.
- Always linked to one or more specific agents.
- Permissions (Administrator, Auditor, Execution) are set per agent.
- Can only be used to access the agents to which they are assigned.
- Only the owner can edit a key's permissions or assign it to agents.
- The same key can be assigned to multiple agents, with different permissions per agent.
- Unassigning a key removes its link to the agent, but does not delete the key.
Global Scope:
- Created from DevTools, not from an agent.
- Not linked to any specific agent; these keys apply to all agents within the tenant or subtenant.
- Permissions are determined by the assigned role for each key.
- Examples of global API Keys include:
- main: Has full administration, audit, and execution permissions for all agents.
- agent-execution: Has execution permission for all agents, but cannot administer or audit.
Note: The
mainandagent-executionkeys are generated automatically by the system and cannot be edited or deleted.
User Permissions
User-based permissions allow you to control which users can manage, audit, or execute an agent. By default, users with certain roles (such as Agent-Administrator, Agent-InstanceUser, Agent-Execution, etc.) have access to all agents. Defining user permissions on an agent allows you to restrict access, so that only explicitly assigned users can operate or manage that agent.
This means:
- Adding users to an agent's permissions restricts access to only those users, overriding the default open access for users with general roles.
- User permissions are a way to lock down sensitive or critical agents to a specific set of people.
- In contrast, API Keys expand access to agents, allowing external systems or users to interact with them in a controlled manner.
How to Add or Assign a User
-
Go to the agent's permissions section.
-
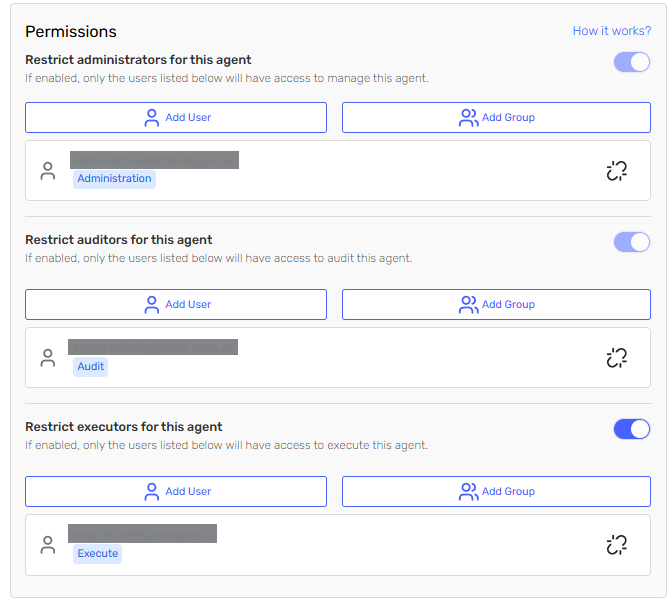
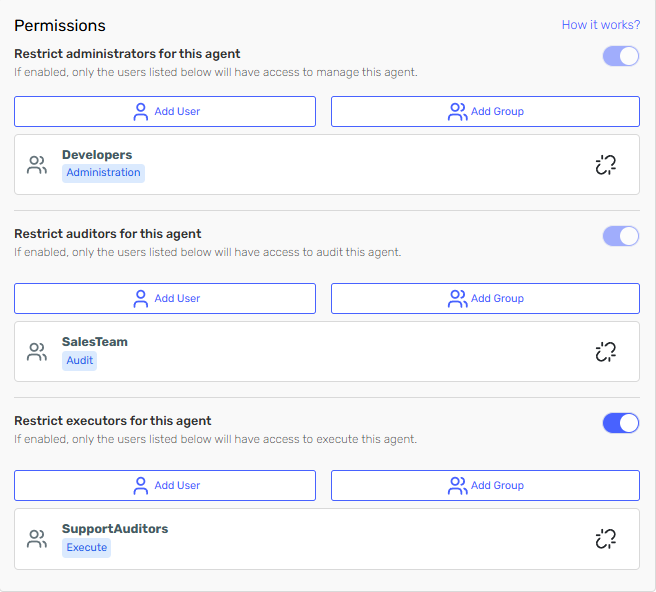
To enable user-based restrictions, activate the restriction toggles for the operation types you want to control:
- Administrator: Toggle to restrict who can manage agent settings and configurations
- Auditor: Toggle to restrict who can view logs and audit information
- Executor: Toggle to restrict who can run the agent
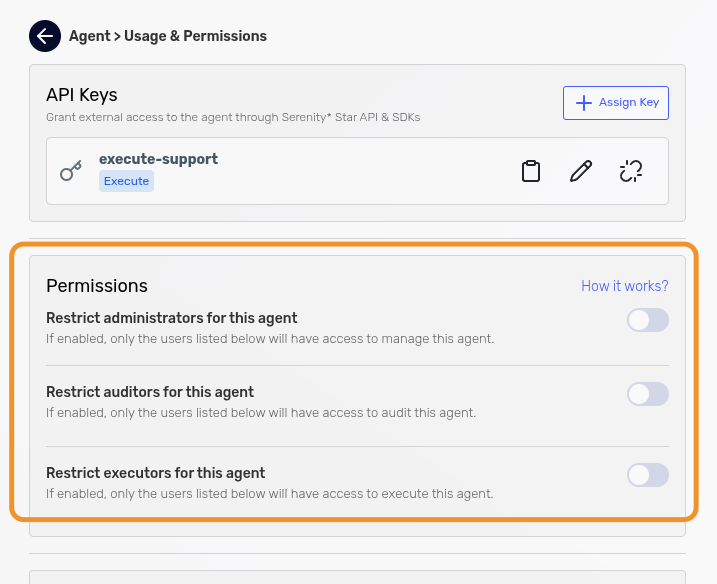
Restrictions have dependencies and work with cascade behavior: you cannot restrict execution without auditing, or auditing without administration. The system automatically enables/disables restrictions to maintain this hierarchy. Additionally, when you enable any restriction, the current user is automatically assigned as Administrator.
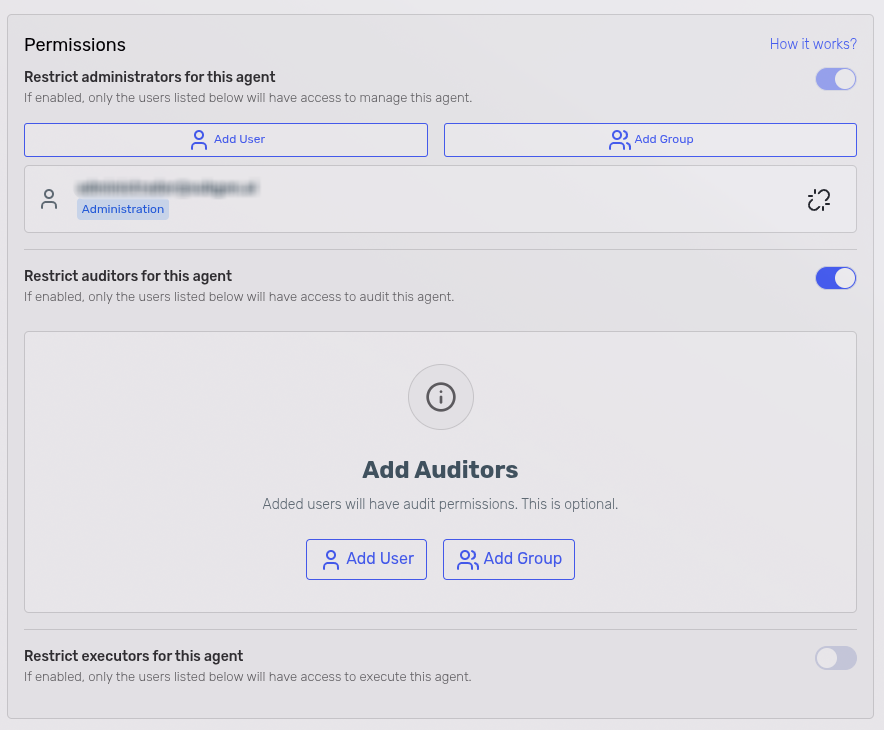
-
Click the Add User button in the corresponding restriction section.
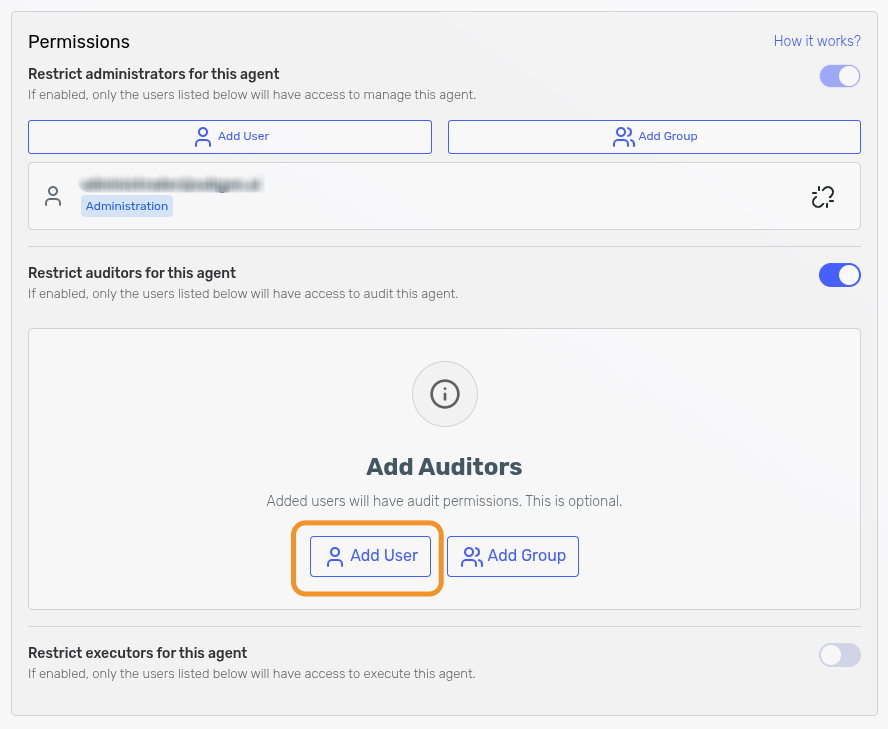
-
A side panel opens with a dropdown listing available users (only users from the same sub-organization are listed). Select the desired user and confirm.
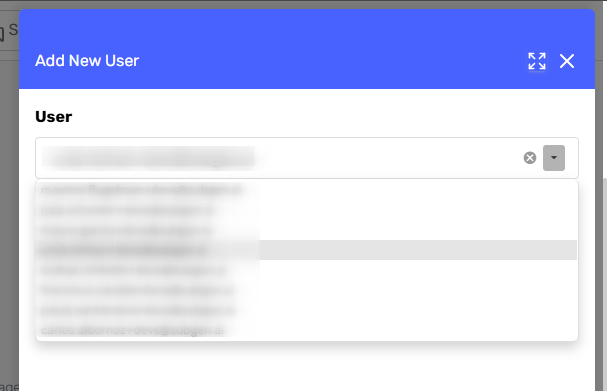
-
The user appears in the permissions list with their assigned permission.
-
Click Save on the agent to persist the permission assignment.
Permission assignments only take effect when you Save the agent configuration.
User Permission Rules
- Each operation type (administration, auditing, execution) can be restricted independently.
- When a restriction is active for an operation, only users with explicit permission for that operation can perform it.
- When no restriction is active for an operation type, users with general roles continue to operate as before.
- There must always be at least one administrator if any restriction is enabled.
- Special roles (TenantAdministrator, SubtenantAdministrator) can always view and edit all agents regardless of user-based restrictions.
- If an agent has assigned users, only those users can operate it according to their permission.
- The permission assigned to a user for an agent takes precedence over their general role.
- You can remove all users if needed, but at least one admin is required if any users are present.
- Agent restrictions for users only apply when using the API with user authentication (username/password) or when navigating within Serenity* Star platform.
- When using the API with an API Key, only the permissions or roles of the API Key are considered, not the user-based restrictions.
Group Permissions
Groups provide a way to assign permissions to multiple users at once. Instead of adding users one by one, you can assign a Group to an agent — all members of the group (both from sub-organizations and individually added users) will inherit the assigned permission level.
To learn how to create and manage groups, see the Groups documentation.
How to Add or Assign a Group
-
Go to the agent's permissions section.
-
To enable group-based restrictions, activate the restriction toggles for the operation types you want to control:
- Administrator: Toggle to restrict who can manage agent settings and configurations
- Auditor: Toggle to restrict who can view logs and audit information
- Executor: Toggle to restrict who can run the agent

Restrictions have dependencies and work with cascade behavior: you cannot restrict execution without auditing, or auditing without administration. The system automatically enables/disables restrictions to maintain this hierarchy. Additionally, when you enable any restriction, the current user is automatically assigned as Administrator.

-
Click the Add Group button in the corresponding restriction section.
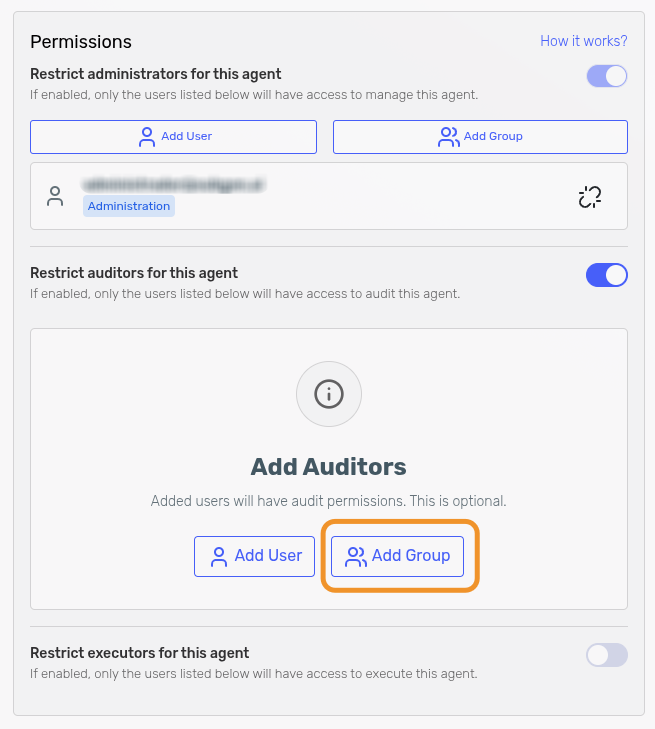
-
A side panel opens with a dropdown listing available groups. Select the desired group and confirm.
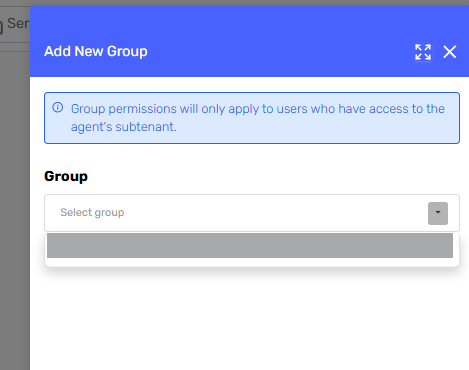
-
The group appears in the permissions list with a distinct group icon to differentiate it from individual users.
-
Click Save on the agent to persist the permission assignment.
Permission assignments only take effect when you Save the agent configuration.
Group Permission Rules
- Groups follow the same permission levels as individual users: Administrator, Auditor, and Executor.
- Group permissions only take effect on users who have access to the agent's sub-organization. Members who do not belong to the sub-organization will not gain access through the group.
- All group members — both from sub-organizations and individually added users — inherit the permission level assigned to the group on the agent.
- A user can receive permissions both individually and via one or more groups. The effective permission is the combination of all granted permissions.
- Removing a group from an agent revokes access for all its members, unless they also have individual permissions.
- Deleting a group from Settings removes it from all agents where it was assigned.
- Group-based permissions follow the same cascade behavior as user permissions: you cannot restrict execution without auditing, or auditing without administration.
Domains
Restricting the origin of requests to specific domains is essential for maintaining control over where and how your AI agents are accessed. Configure a list of allowed domains to ensure that agents only respond to requests from trusted sources.
- Restrict Origin: Specify which domains are permitted to interact with your agents, blocking requests from unapproved sources.
- Manage Allowed Domains: Easily add or remove domains from the approved list as needed to maintain security compliance.
A header with the key Origin must be included in the request, specifying the origin of the request.
Example: If the allowed domain is https://www.mywebpage.com, the following origins would be permitted:
https://www.mywebpage.comhttps://mywebpage.com/subdomainhttps://subdomain.mywebpage.com
Execution Limits
Execution limits help manage resource usage by setting constraints on how frequently an agent can execute tasks, ensuring optimal performance and preventing system overload.
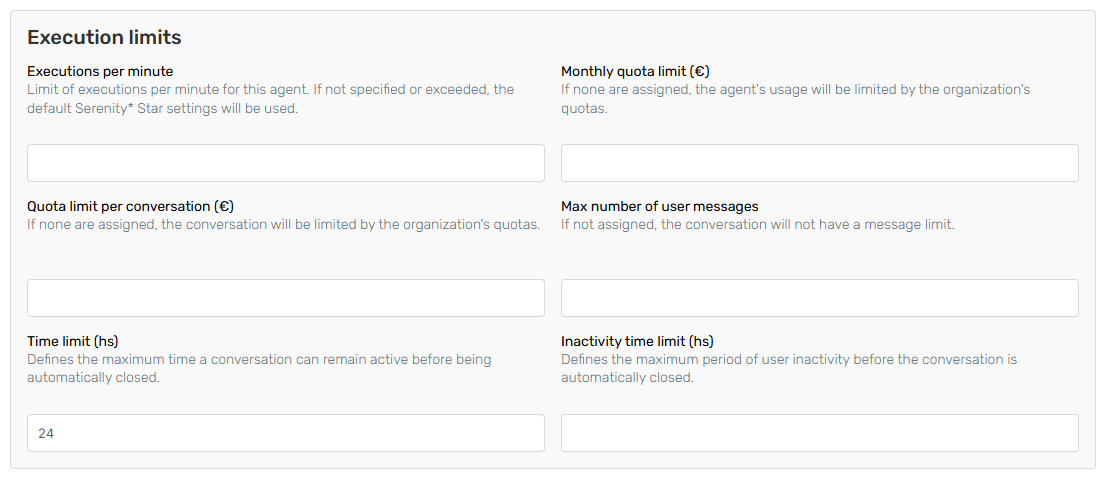
- Executions Per Minute: Limit the number of agent executions allowed per minute to prevent excessive use.
- Monthly Quota Limit: Define a maximum monthly quota to control costs.
- Quota Limit Per Conversation (Assistant agents only): Define a maximum quota for each conversation to control costs.
- Maximum Number of User Messages (Assistant agents only): Set an upper limit on messages a user can send within the same conversation.
- Monthly Quota Limit: Establish a monthly maximum limit for agent usage to manage overall consumption.
- Inactivity Time Limit: Maximum period of inactivity before the conversation is automatically closed
Best Practices
- Regularly review assigned keys, users, and groups.
- Use the minimum necessary permission level.
- Remove access that is no longer needed.
- Prefer groups over individual user assignments when multiple users need the same access level.
- Review group compositions when modifying agent permissions to ensure only the right people retain access.
- Set execution limits to prevent resource overconsumption, ensure fair usage, and optimize efficiency.