Advanced ATM Security Assistant
Introduction
In high-risk environments such as Automated Teller Machines (ATMs), the need to detect suspicious behavior in real time is critical. This article explores a concrete use case: extending an existing helmet-detection system with a natural language agent (LLM) that interprets, classifies, and responds to risk scenarios captured in images.
From Visual Detection to Semantic Understanding
The system builds upon an already functional infrastructure that identifies individuals wearing helmets. On top of this, an "activity agent" is trained with a specific prompt designed to:
- Analyze images for unlawful or suspicious behavior
- Classify the event (e.g., armed robbery, forced entry, vandalism)
- Count and describe individuals (age, gender, clothing, height, tattoos)
- Generate a structured JSON output with tags, confidence scores, timestamps, and recommended actions
Step-by-Step Agent Setup in Serenity* Star
Creating this kind of agent in Serenity* Star is straightforward. Below is a visual walkthrough:
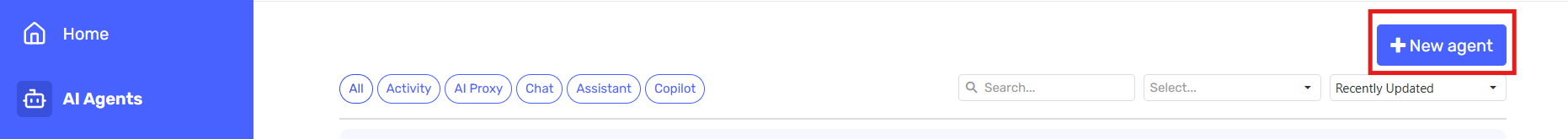
-
Create a new agent
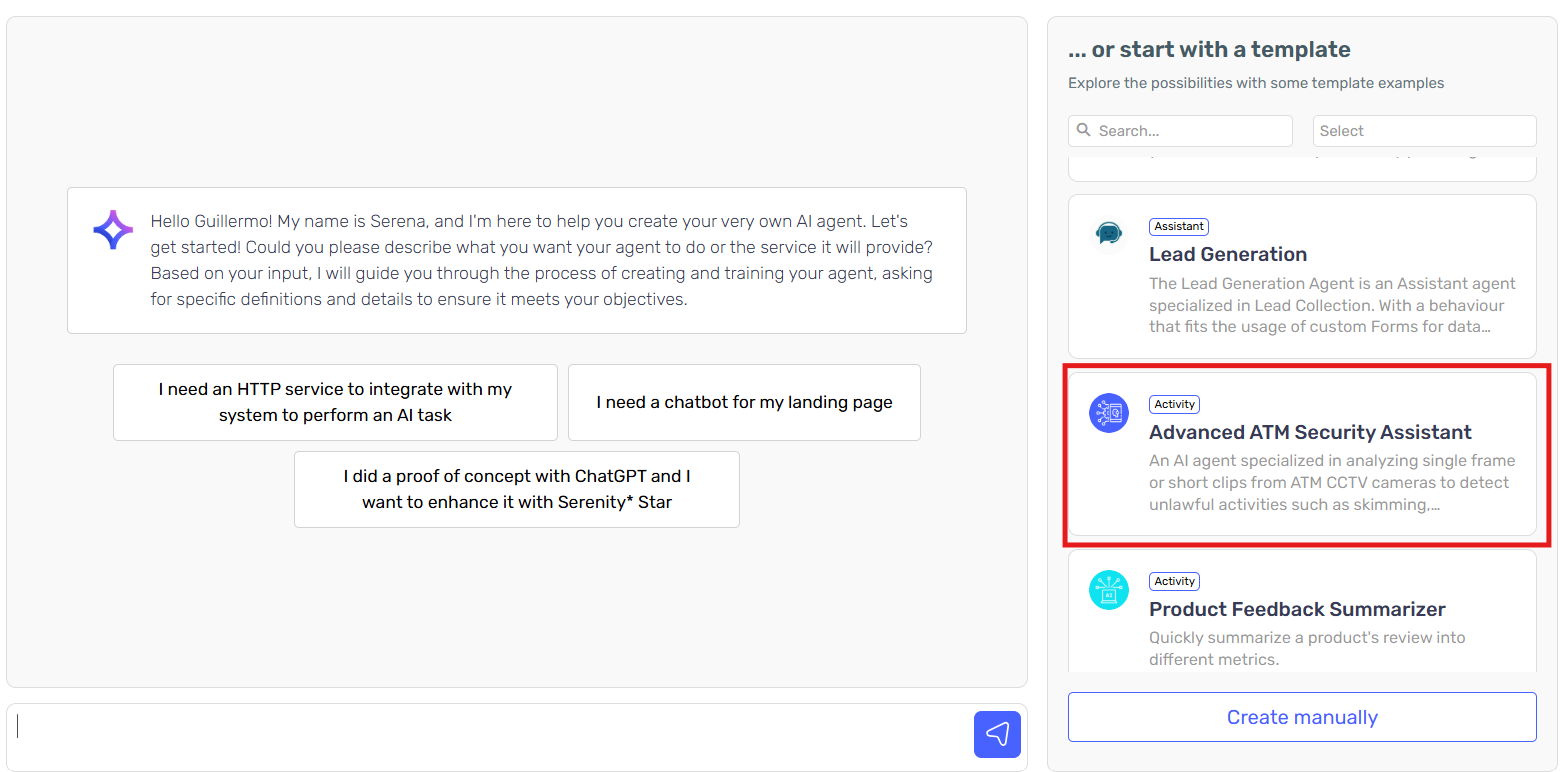
-
Select the 'Advanced ATM Security Assistant' template
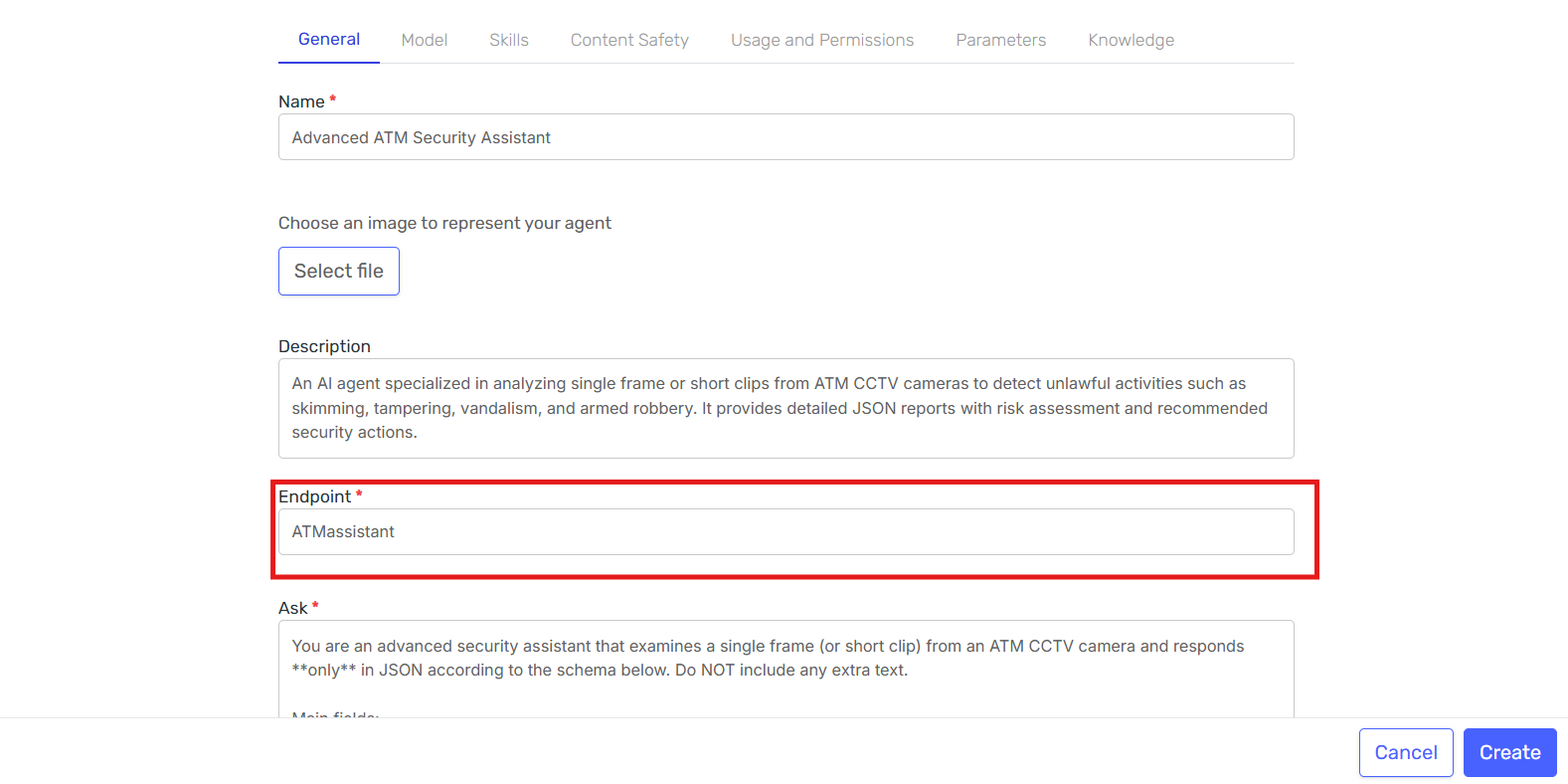
-
Customize the endpoint name and configuration
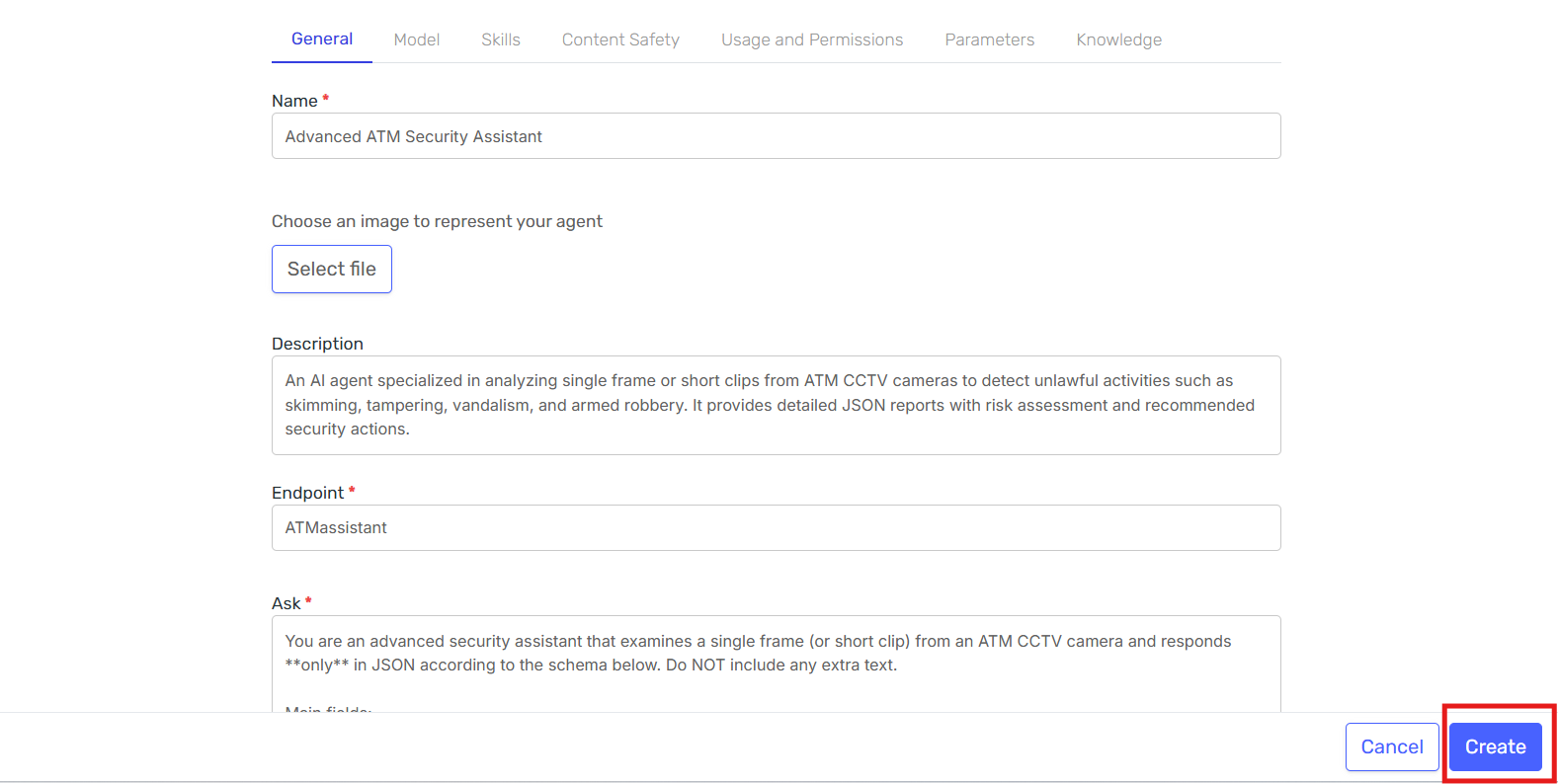
-
Finalize creation
-
Enable image processing capabilities
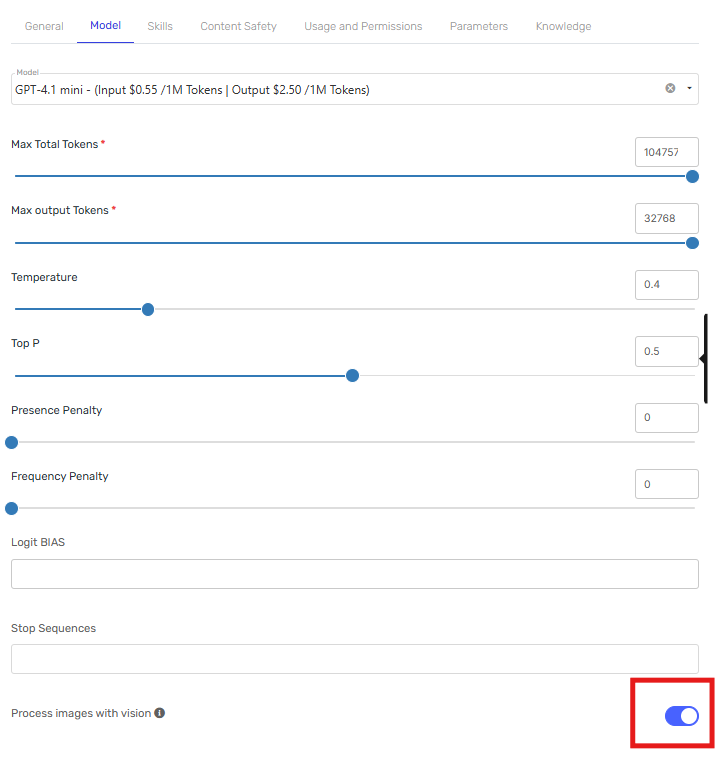
-
Upload an image to test the agent
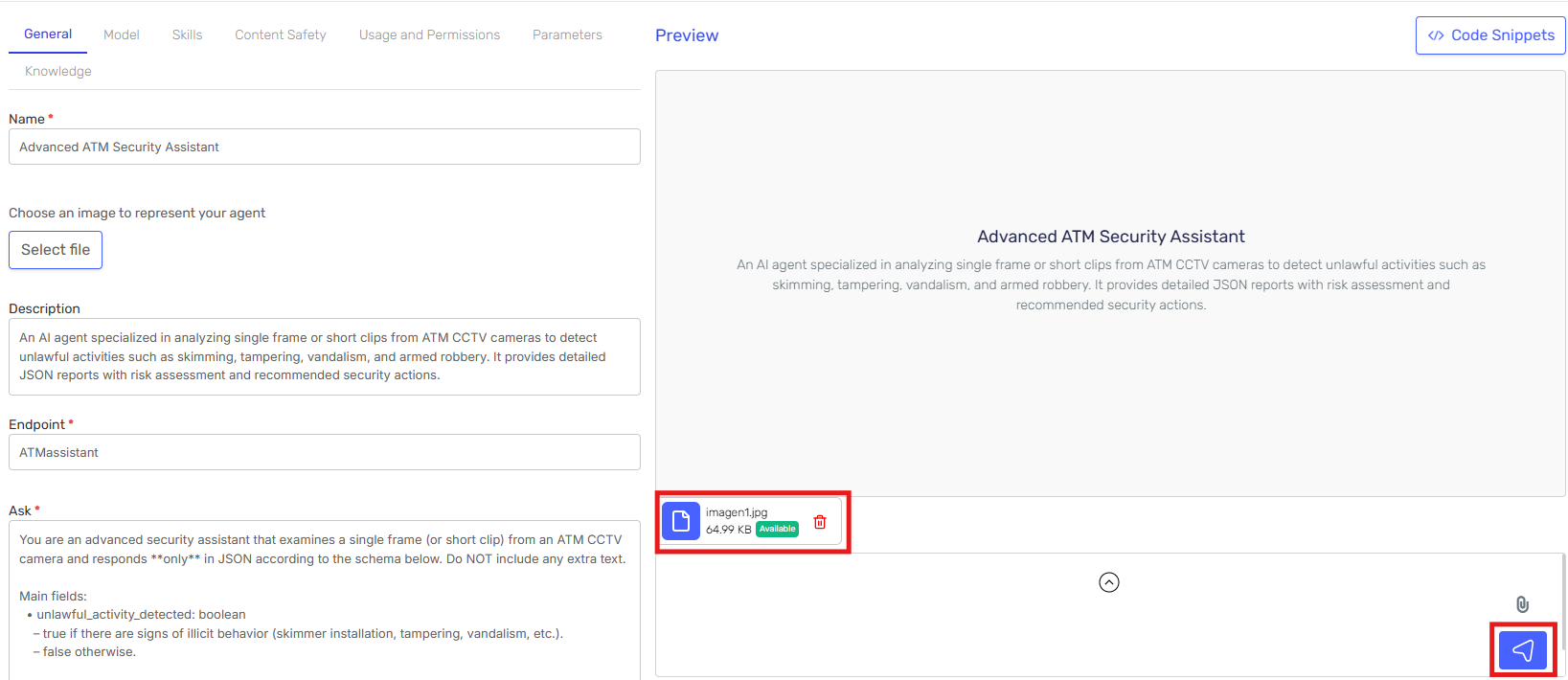
Execution and Results
Once deployed, the agent can analyze ATM surveillance images with impressive speed and accuracy.
-
Test Image 1 – Normal ATM usage scenario:
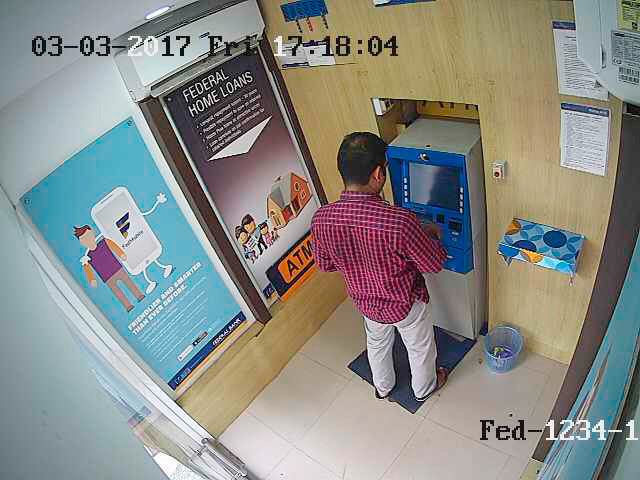
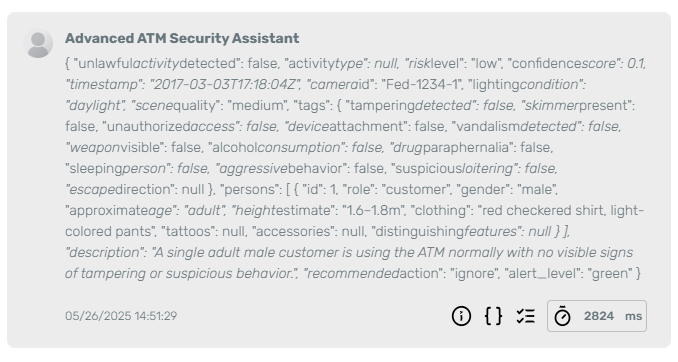
The system correctly identifies that no unlawful activity is occurring, with a low-risk score and a recommendation to ignore.
-
Test Image 2 – Forced entry attempt:

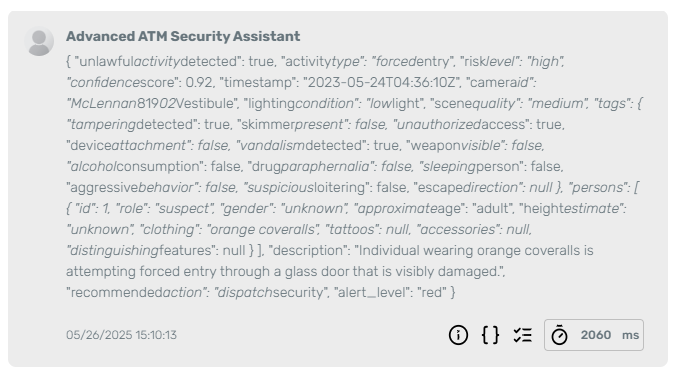
Here, the agent classifies the situation as “forced entry,” detects visible vandalism, and recommends dispatching security with a high-confidence score.
-
Test Image 3 – Attempted ATM break-in with tools:
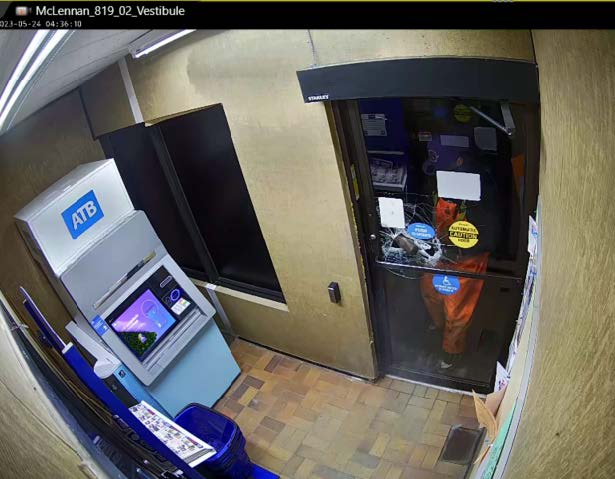
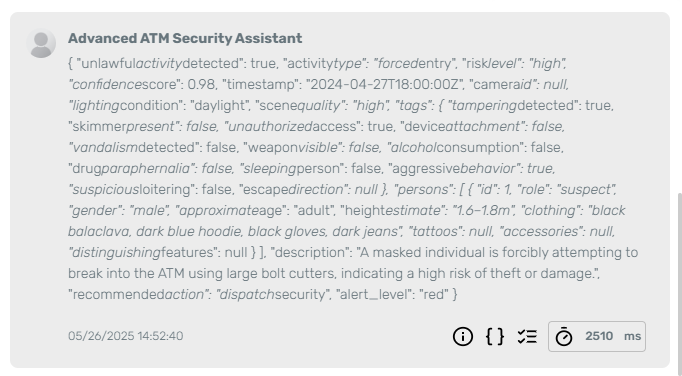
The agent detects a masked suspect attempting to breach the ATM using bolt cutters, with high alert level and immediate action recommendation.
Integration with Serenity* Star
The activity agent operates entirely within Serenity* Star, enabling seamless monitoring and continuous refinement of its performance. Once deployed, it enables:
- Centralized incident management across multiple camera feeds
- Automated action flows (alerts, escalations, reports)
- Continuous training via real-world feedback loops
API Access and Execution
To retrieve the API Key and execute the agent via code, Serenity* Star provides auto-generated code snippets. Here's how to find and use them:
-
Step 1: Locate the "Code Snippets" section in the agent configuration
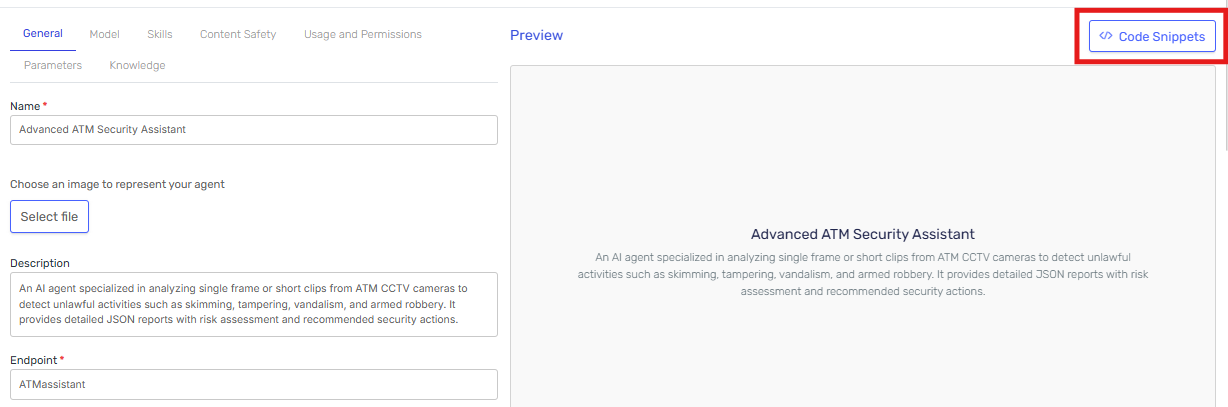
-
Step 2: Copy the cURL command to execute your agent via API
Systems Integration with Serenity* Star
-
Upload the images to analyze to AI Hub through the volatile knowledge endpoint:
Upload Volatile Knowledgecurl --location 'https://api.serenitystar.ai/api/v2/VolatileKnowledge' \
--header 'X-API-KEY: <YOUR_API_KEY>' \
--form '<YOUR_IMAGE_FILE>' -
Check image processing status:
Check Volatile Knowledgecurl --location 'https://api.serenitystar.ai/api/v2/VolatileKnowledge/<VOLATILE_KNOWLEDGE_ID>' \
--header 'X-API-KEY: <YOUR_API_KEY>' -
Execute the agent with the uploaded image ID:
Execute Agentcurl --location 'https://api.serenitystar.ai/api/v2/agent/ATMassistant/execute' \
--header 'Content-Type: application/json' \
--header 'X-API-KEY: <YOUR_API_KEY>' \
--data '[{
"Key": "volatileKnowledgeIds",
"Value": ["<YOUR_IMAGE_VOLATILE_KNOWLEDGE_ID>"]
}]' -
Integrate the resulting JSON response with your target system.
Conclusion
This use case demonstrates how combining LLMs with computer vision elevates security from passive monitoring to intelligent, operational interpretation. By generating structured, actionable insights in real time, Serenity Star is ready to scale these solutions into critical infrastructure environments.
